
Website NFC Tag Messages Meaning, and Can You Stop Them?
This article explains the meaning of a message or alert with ‘Website NFC tag’ or ‘NFC Tag Detected’, the meaning of related messages, and what to do if you want to stop those messages. They can appear on your phone and might confuse or annoy you. However, they can also be useful. To understand, use,…
3 Reasons Why You Should Invest In A GPS Tracker
Are you wondering why you should invest in a vehicle GPS tracker? I previously worked on a site where the terrain could be difficult. It could be dangerous, so there was a major effort put into journey management. A GPS tracker was part of that safety management system. Why else might you invest in such…

Cybersecurity Tips for Online Gamers
Cybersecurity Tips for Online Gamers Here are three Cybersecurity tips for online gamers. Online gamers spend more time on the web and engage in more activities compared to the average user. This is why they’re particularly vulnerable to cyber attacks. For instance, there’s been a recent surge in incidents of Trojan malware. These are being…
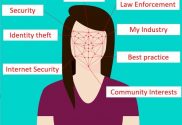
10 facial recognition software guidelines
10 Facial Recognition Technology Guidelines Facial recognition software is becoming more prevalent and five facial recognition guidelines were proposed by Amazon’s Michael Punke (Amazon Web Services’ VP of Global Public Policy). A further 5 are proposed here to make a total of 10 facial recognition technology guidelines to be applied more broadly. Facial recognition software…

How to Protect Your Clients’ Data and Make Money Doing it
As you may have seen by now, Cryptolocker has infected around 250,000 PCs so far and is still going strong. If you aren’t familiar with Cryptolocker, it’s a business owner’s worst nightmare. Once installed, Cryptolocker will encrypt files on the machine it is installed on as well as all network drives that machine is connected…
How to Scan a Network For Port Vulnerabilities
Have you ever wondered how secure a network that you set up actually is? Today I would like to share a tool with you that will allow you to easily scan a network for external port vulnerabilities. This tool is called ShieldsUp! and is web based which allows your scan to take place outside of…
How to Disable Windows Vista Permission Security Prompts
![]() If you have been using Windows Vista for a while then you probably know how annoying the security confirmations can be. Any time you install a program, install drivers, run programs that need administrative rights, change certain configuration settings, etc., you are forced to confirm your actions before continuing. Fortunately, there are ways to disable these prompts.
If you have been using Windows Vista for a while then you probably know how annoying the security confirmations can be. Any time you install a program, install drivers, run programs that need administrative rights, change certain configuration settings, etc., you are forced to confirm your actions before continuing. Fortunately, there are ways to disable these prompts.

Latest Comments