Have you ever wondered how secure a network that you set up actually is? Today I would like to share a tool with you that will allow you to easily scan a network for external port vulnerabilities. This tool is called ShieldsUp! and is web based which allows your scan to take place outside of your firewall. Just follow these steps to begin.
![]() credit: br1dotcom
credit: br1dotcom
Step 1: Go to https://www.grc.com/x/ne.dll?bh0bkyd2.
Step 2: When you are ready to begin, click the “Proceed” button.
Step 3: Now choose the ports you would like it to scan. To scan all ports click “All Service Ports.”
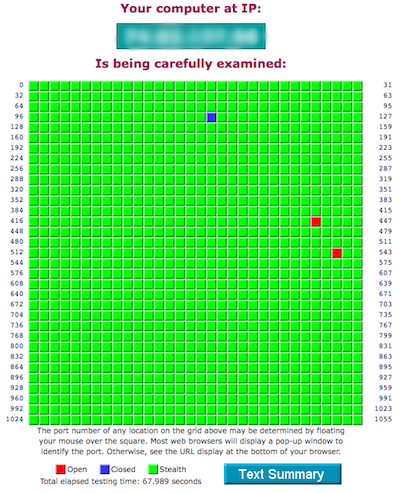
When the scan is finished you will see a color-coded graphical display of all your ports as well as a summery . Ports in green are stealth, ports in blue are closed, and ports in red are open. You can also put your mouse over each port to get a short description.
Now you can use this information to close any of these open ports in your firewall. What other tools do you like to use to help prevent network vulnerabilities?


Leave A Response